Nowadays, electronic security and privacy are becoming increasingly important to users. Security and privacy in communication networks are usually provided by cryptographic algorithms. Security is based on three main concepts:
- Confidentiality: a feature that guarantees that attackers cannot read data,
- Integrity: a feature that guarantees that attackers cannot modify data during a transfer, and
- Authenticity: a feature that guarantees that attackers cannot impersonate valid users.
There are many proven ciphers that provide these Confidentiality, Integrity and Authenticity (CIA) features individually and even together in a single algorithm. The most popular standardized algorithms are Advanced Encryption Standard (AES) [1] for encryption (providing confidentiality), Secure Hash Function (SHA) [2,3] for computing message digests (providing integrity), and (Elliptic Curve)Digital Signature Algorithm (EC)DSA [4] for digital signatures (providing authenticity).
The examples of algorithms mentioned above are integrated into cryptographic protocols that provide security features to users in communication systems. Most of these algorithms may be used in standard communication systems that involve servers, computers, mobile phones, etc. However, in heterogeneous networks, such as Internet of Things (IoT) and Supervisory Control and Data Acquisition (SCADA), there are also different types of devices, usually with very restricted computational and memory resources. As examples, we name sensors, controllers, wearable devices, cyber-physical devices, and medical aids. On such devices with very limited computational power, it is very difficult to use advanced cryptographic algorithms without affecting the fundamental functions. In most cases, the use of asymmetric ciphers (such as RSA, DSA or DH algorithms) is not supported by the CPUs and micro controllers and is very difficult to implement in software due to lack of computational power.
The situation gets even worse in case we need to implement privacy-preserving features on constrained devices. Even the fundamental building block for privacy-enhanced authentication, the group signatures [5-7], is based on asymmetric cryptography and operations that are at least as complex as digital signatures. More advanced cryptographic schemes, such as Attribute-Based Credentials (ABCs) [8-10] or Homomorphic Encryption (HE) [11-13] can be used to protect user privacy.
Using anonymous Attribute-Based Credentials (ABCs), users can prove their personal attributes (such as age, citizenship, ticket ownership, negative SARS-CoV-2 test) without revealing their identity. Furthermore, advanced privacy-enhancing features are provided by ABC schemes, such as unlinkability, untraceability or selective attribute disclosure.
With the increasing popularity of IoT and industrial networks, as well as the increase of computing power in wearable devices, we cannot ignore security and privacy protection in real applications anymore. Collaborative Indoor Positioning Systems (CIPSs) are a good example of a real application where the security and privacy of users is currently highly compromised. [14] propose a new decentralized privacy-preserving user authentication mechanism for CIPSs with ABC. The solution combines zero-knowledge proofs with a revocation scheme based on lifetime and provides anonymity, unlinkability, and untraceability. The benchmarks are shown in the following figure.
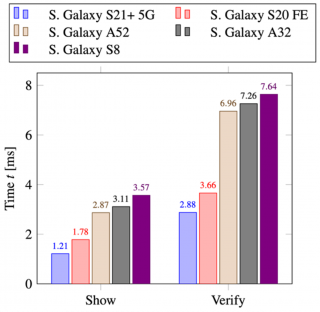
As can be seen, the scheme is divided into two algorithms, which are executed in various smart phones to evaluate the performance and speed. We can see the execution of both algorithms takes slightly more than 10ms on the slowest device without including the communication overhead.
[1] Joan Daemen and Vincent Rijmen. Reijndael: The advanced encryption standard. Dr. Dobb’s Journal: Software Tools for the Professional Programmer, 26(3):137–139, 2001.
[2] Wouter Penard and Tim van Werkhoven. On the secure hash algorithm family. Cryptography in Context, pages 1–18, 2008.
[3] Guido Bertoni, Joan Daemen, Michaël Peeters, and Gilles Van Assche. The keccak sha-3 submission. Submission to NIST (Round 3), 6(7):16, 2011.
[4] Thomas Pornin. Deterministic usage of the digital signature algorithm (dsa) and elliptic curve digital signature algorithm (ecdsa). Internet Engineering Task Force RFC, 6979:1–79, 2013.
[5] Jan Camenisch and Markus Stadler. Efficient group signature schemes for large groups, pages 410–424. Springer Berlin Heidelberg, 1997.
[6] Dan Boneh and Xavier Boyen. Short signatures without random oracles and the SDH assumption in bilinear groups. Journal of Cryptology, 21(2):149–177, Apr 2008.
[7] San Ling, Khoa Nguyen, Huaxiong Wang, and Yanhong Xu. Constant-size group sig- natures from lattices. In IACR International Workshop on Public Key Cryptography, pages 58–88. Springer, 2018.
[8] Jan Camenisch, Stephan Krenn, Anja Lehmann, Gert Læssøe Mikkelsen, Gregory Neven, and Michael Østergaard Pedersen. Scientific comparison of ABC protocols. 2014.
[9] Jan Hajny and Lukas Malina. Unlinkable Attribute-Based Credentials with Practical Revocation on Smart-Cards, pages 62–76. 2013.
[10] Jan Camenisch, Manu Drijvers, and Jan Hajny. Scalable revocation scheme for anony- mous credentials based on n-times unlinkable proofs. In Proceedings of the 2016 ACM on Workshop on Privacy in the Electronic Society, WPES ’16, pages 123–133, New York, NY, USA, 2016. ACM.
[11] Craig Gentry and Dan Boneh. A fully homomorphic encryption scheme, volume 20. Stanford university Stanford, 2009.
[12] Abbas Acar, Hidayet Aksu, A Selcuk Uluagac, and Mauro Conti. A survey on homo- morphic encryption schemes: Theory and implementation. ACM Computing Surveys (CSUR), 51(4):1–35, 2018.
[13] Ilaria Chillotti, Nicolas Gama, Mariya Georgieva, and Malika Izabachène. Tfhe: fast fully homomorphic encryption over the torus. Journal of Cryptology, 33(1):34–91, 2020.
[14] Raúl Casanova-Marqués, Pavel Pascacio, Jan Hajny, and Joaquín Torres-Sospedra. Anonymous attribute-based credentials in collaborative indoor positioning systems. In Proceedings of the 18th International Conference on Security and Cryptography – SECRYPT, pages 791–797. INSTICC, SciTePress, 2021.
The security-related benchmarks for increasing the anonymization strategies and security of wearable devices could be found in A-WEAR’s GitHub. In particular (as of the milestone achievement):
- C implementation of the RKVAC (Revocable Keyed-Verification Anonymous Credentials) protocol;
- C implementation (user side) of the RKVAC (Revocable Keyed-Verification Anonymous Credentials) protocol for MULTOS smart cards;
- Cryptographic protocols for Confidentiality, Authenticity and Privacy on constrained devices.
Those are supported by scientific publications available at Zenodo.